The goal of Industry 4.0 is to provide a smarter and more efficient future, where machines communicate at increasingly faster speeds, processes optimize in real time, and production dynamically adapts to market demands.
No entanto, a interconexão que torna tudo isso possível também abriu a porta para um novo e perigoso vetor de risco para os sistemas de automação e controle, as vulnerabilidades de segurança. A cibersegurança em sistemas de controle industrial (ICS) e tecnologia operacional (OT) difere das ameaças tradicionais, que visavam a extração de dados, e que agora , buscam interromper processos físicos, danificar equipamentos e, em casos extremos, colocar em risco vidas humanas.
The root of this challenge lies in the convergence of IT (Information Technology) and OT networks. What were once “isolated islands” of automation are now connecting to the corporate network and, in many cases, the internet. The need to optimize production through data analysis and remote maintenance caused this fusion.
But control systems, which were developed to operate on closed networks and with a focus on availability, are now exposed to threats that were not in their original design, such as malwares, phishing attacks, and denial of service. The risk has migrated from the digital to the physical dimension, making interruptions potentially catastrophic.
The industry therefore needs The industry therefore needs a new set of principles and tools designed for this new security context. The answer to this need comes in the form of the ISA/IEC 62443 standarda standard of excellence that defines a detailed system for managing risks, implementing safeguards, and ensuring security throughout the entire lifecycle of industrial control systems.
The theory behind the applied protection: detailing the ISA/IEC 62443
The ISA/IEC 62443 standard is a comprehensive series of documents that addresses the cybersecurity of industrial automation and control systems, where security is not viewed as a single product, but as an integrated approach involving technology, architecture, and, fundamentally, people and processes. This approach is the essence of security-by-design, which integrates security from the initial phases of system and software development.The documents are divided into 4 parts that present different aspects of the lifecycle of automation and control systems:
- – Part 1 (general): provides an overview of the essential terms and concepts that are the basis of the standard series.
- – Part 2 (policies and procedures): highlights the importance of governance and operational processes. It establishes guidelines for creating a cybersecurity program and managing security.
- – Part 3 (systems): offers guidance for the design and implementation of secure systems, including network architecture.
- – Part 4 (components): describes the technical requirements that components, such as programmable controllers, must meet to be considered secure.
The pillar of system security, according to the standard, is supported by 7 fundamental requirements (FRs), which serve as the basis for the security of any system:
- – FR1 - Identification and Authentication Control (IAC): determines who is permitted to access the system.
- – FR2 - Use Control (UC): defines what an authorized user can do, limiting their actions to the minimum necessary.
- – FR3 - System Integrity (SI): ensures that the system is free from manipulation and that its functionality has not been compromised.
- – FR4 - Data Confidentiality (DC): ensures that sensitive information, such as the source code, remains confidential.
- – FR5 - Restricted Data Flow (RDF): controls and limits communication between different parts of the system.
- – FR6 - Timely Response to Events (TRE): enables rapid response to incidents through event monitoring and auditing.
- – FR7 - Resource Availability (RA): ensures that the system remains operational and resists denial of service attacks.
These requirements are not independent; they interconnect to form a cohesive and integrated protection ecosystem. For example, the ability to generate logs (FR2) becomes more valuable when there is good user management (FR1), which ensures that the logs have audit value (FR6).
The standard also classifies the robustness of a system to face different threats through 4 security levels (SLs):
- – Level 1 (SL1): protects against accidental misuse or low-impact threats.
- – Level 2 (SL2): protects against intentional attacks that use simple means, such as scripts or brute force.
- – Level 3 (SL3): protects against more elaborate attacks with moderate resources.
- – Level 4 (SL4): protects against threats with vast and sophisticated resources.
The choice of a security level for a system is not arbitrary; it is the result of a risk assessment. The standard does not impose an "SL4 for everyone," but guides companies to determine the appropriate level of protection for their assets. This allows for smart and targeted investment in cybersecurity.
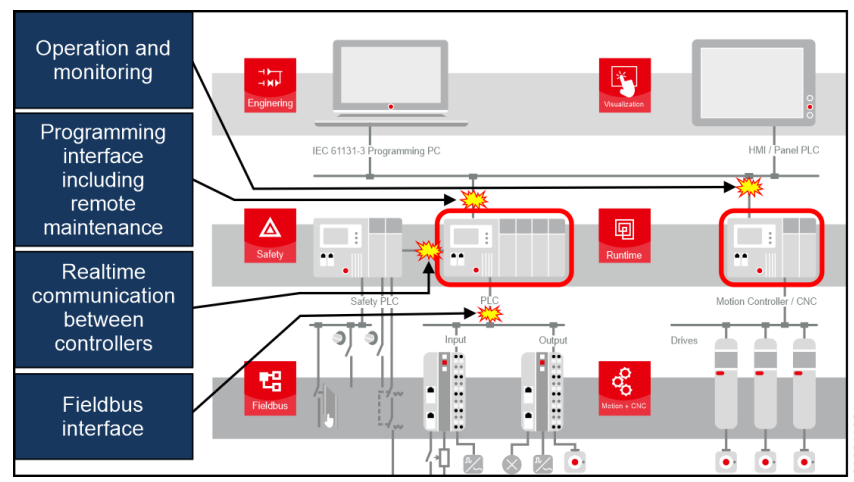
The layered architecture is a fundamental concept in OT security. The Purdue Reference Model, adopted by ISA-99, is the conceptual basis for segmenting industrial networks. The model divides networks into hierarchical layers, from the factory floor (levels 0 and 1, which contain sensors, actuators, and PLCs) up to the corporate network (levels 4 and 5). And the ISA/IEC 62443 model deepens this concept by defining Zones logical or physical segments where security is applied) and Conduits (the communication paths between zones). This architecture aims to isolate critical systems from potential threats and control the flow of data.
Cybersecurity policies and Altus controllers
Altus, by integrating security features into its controllers and software, translates the ISA/IEC 62443 theory into a practical solution:
User and access management (aligned with FR1 and FR2)
The security of a system begins with managing who has access and what that person can do. Our programming software, MasterTool,offers management that enables the creation of user accounts for each person involved in the project and organization into groups. Permissions can be configured for menu commands, object types(like POUs and GVLs), and specific objects, ensuring that intellectual property and application integrity are protected. Authentication is protected by mechanisms such as obscuring passwords with asterisks during login and configuring the maximum number of authentication attempts to prevent attacks.
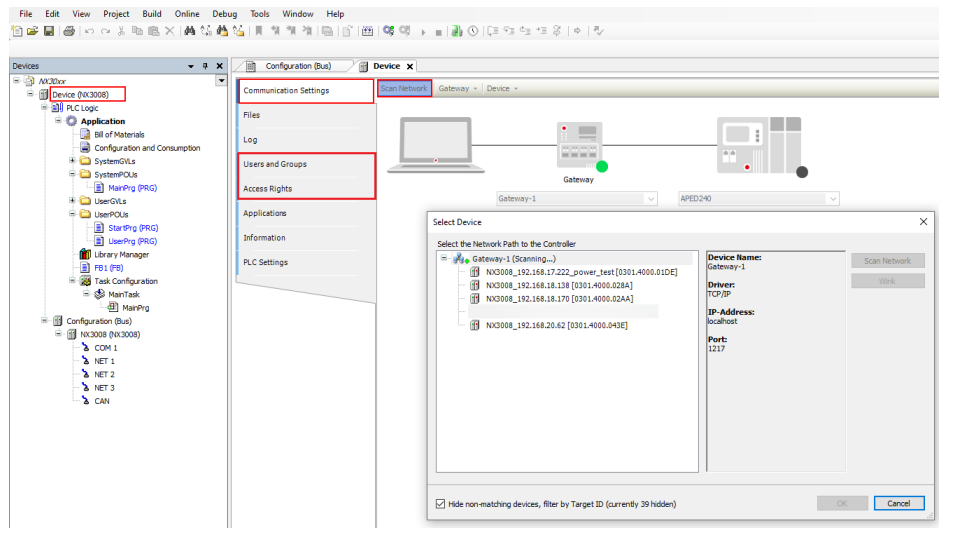
Altus’ PLCs, including the Nexto NX, Nexto XP, and HX (Xtorm) series, have a user permission management system for the CPU. Access rights can be defined for specific objects, limiting the range of functionalities for each group. The standard groups(Administrator, Developer, Everyone, Service, Watch)enables efficient permission management based on roles. Authentication for online access is protected by encryption, ensuring that only authorized users can execute commands like stopping the application.
Data protection and integrity (aligned with FR3 and FR4)
Protection of the application's source code is a priority, as it contains the manufacturer's intellectual property and detailed information about the system. MasterTool offers source code encryption via passwords or physical security keys (USB Dongle).The use of X.509 certificates for encryption is also an option, ensuring that the code can only be accessed by users with the correct public key.
Software integrity is guaranteed by the ability to sign compiled IEC libraries.Signing with an X.509 certificate enables the verification of the code's authenticity and integrity, preventing the use of malicious or modified libraries.
Additionally, the secure OPC UA Server of Altus’ controllers supports encrypted communication with X.509 certificates,protecting the confidentiality and integrity of data exchanged with connected clients. Communication with the WebVisu interface can also be encrypted with HTTPS to prevent data interception, reinforcing network security.
Network security and restricted data flow (aligned with FR5)
Altus, by providing an integrated firewall in the PLCs and VPN support,allows the "Zones and Conduits" principles of the 62443 standard to be implemented in practice. The firewall filters data packets based on interfaces, ports, protocols, and source and destination addresses, protecting the device against flood-type attacks.The presence of a firewall at the controller level (Purdue Model levels 1 and 2) prevents an attack on a higher layer (IT) from propagating to the control layer.
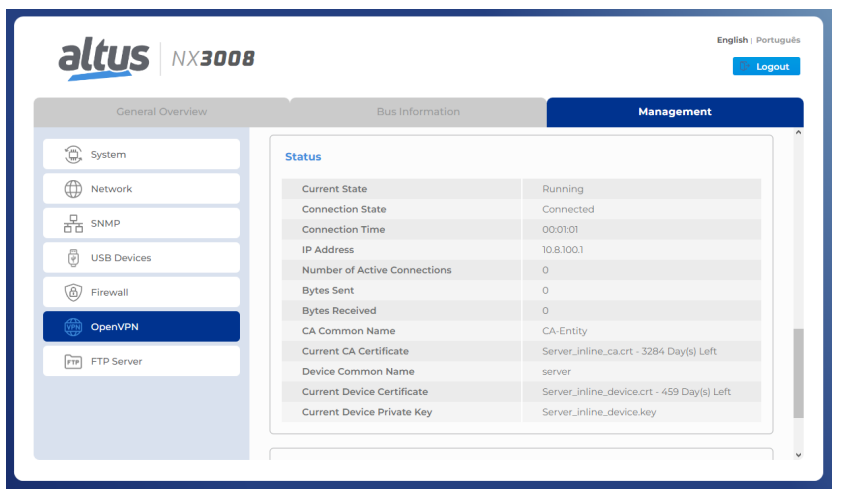
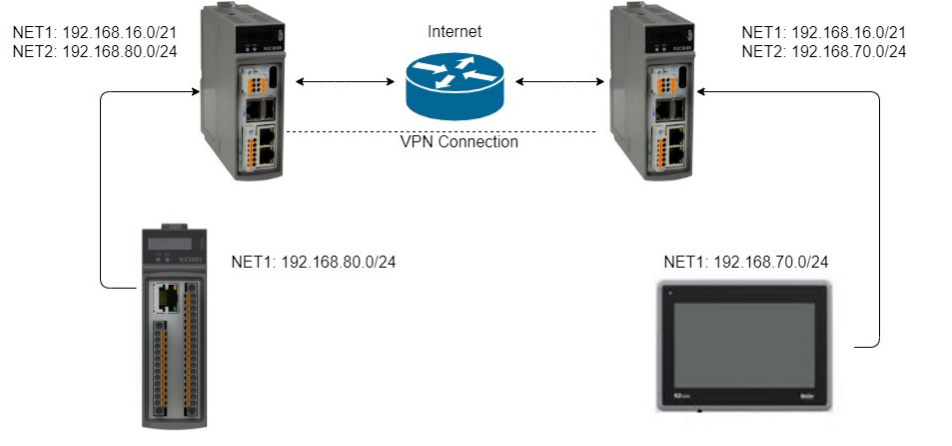
The integrated OpenVPN enables the creation of a secure communication tunnel over untrusted networks, essential for remote maintenance and connecting multiple branch offices. The supported network architectures Host-to-Host, Host-to-Site and Site-to-Site are solutions to the challenge of enabling secure external access without exposing the OT network to the internet, transforming the controller into a tool for implementing an advanced defense architecture.
Monitoring and availability (aligned with FR6 and FR7)
Operational resilience is just as important as preventing attacks. Altus focuses on ensuring that the system can remain operational and quickly recover from failures or incidents. The detailed logs of MasterTool record errors, failures, and user actions, providing essential data for investigation and incident response. The system's backup and recovery capability enables configuration data, source code, and firmware to be saved and restored to a known functional state, minimizing downtime and losses.
Protection against denial of service attacks, which seek to overload the controller with traffic, ensures system availability. Furthermore, the deterministic output functionality defines the behavior of outputs in case of controller stoppage, ensuring process safety and mitigating risks.
Compliance with transparency
Industrial cybersecurity has moved from being a secondary concern to a strategic pillar of modern industry. In a world where interconnection is the norm, the protection of industrial control systems (ICS) and operational technology (OT) is essential for business continuity, employee safety, and business resilience. The cybersecurity journey does not have an endpoint; it is a continuous process of evaluation, implementation, and improvements.
The ISA/IEC 62443 standard goes beyond a checklist: it is a guide for the full operation of industrial operations. Its systemic structure establishes clear responsibilities for everyone involved and defines the essential technical and procedural requirements for building safer and more resilient environments.
Altus, through its cybersecurity policy and the incorporation of advanced features into its controllers and software, reinforces our permanent commitment to the protection of our clients. Our ecosystem of solutions includes everything from user and privilege management, data encryption, and network security with firewall and VPN, to operational resilience guaranteed by logs and backup routines, as seen throughout this article. In this way, we offer the necessary tools to implement defense architectures in full compliance with the principles of ISA/IEC 62443.
Furthermore, transparency regarding the level of compliance, including an honest discussion about eventual gaps, and adherence to applicable regulations, as you can see on our cybersecurity page,consolidate Altus as a strategic partner in the digital future of industry.
After all, security is not just in the equipment, but in the joint construction of technological solutions for increasingly reliable and secure applications for all industrial sectors.
Read our Cybersecurity Policy Manual by downloading it here












